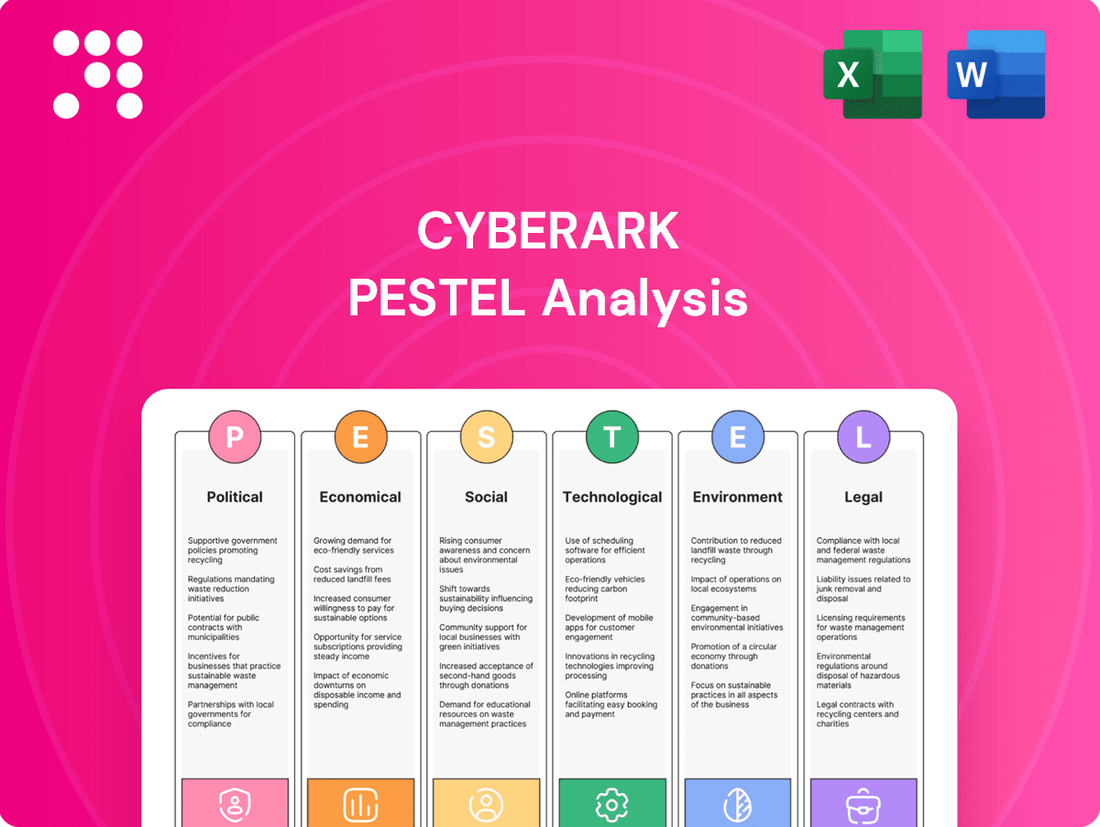
CyberArk PESTLE Analysis
Fully Editable
Tailor To Your Needs In Excel Or Sheets
Professional Design
Trusted, Industry-Standard Templates
Pre-Built
For Quick And Efficient Use
No Expertise Is Needed
Easy To Follow
CyberArk Bundle
Uncover the critical political, economic, social, technological, legal, and environmental factors shaping CyberArk's trajectory. Our expertly crafted PESTLE analysis provides the deep-dive insights you need to anticipate market shifts and identify strategic opportunities. Download the full version now to gain a competitive edge.
Political factors
Government cybersecurity policies, such as the EU's NIS2 Directive enacted in late 2022 and the US Cybersecurity Improvement Act of 2023, directly drive demand for robust identity security solutions like those offered by CyberArk. These regulations mandate stronger protections for critical infrastructure and data, compelling organizations to invest in advanced access management. Increased government spending, with the US alone allocating an estimated $11.9 billion to cybersecurity in its FY2024 budget, presents significant opportunities for companies specializing in privileged access management (PAM), a core CyberArk offering.
Political stability and geopolitical tensions also play a crucial role. For instance, ongoing cyber threats and state-sponsored attacks reported throughout 2023 and into early 2024 have elevated cybersecurity to a top national security priority globally, leading to expanded budgets and a greater focus on securing digital identities and privileged accounts across both public and private sectors.
International trade relations significantly shape CyberArk's global reach. For instance, the US-China trade tensions, ongoing through 2024 and into 2025, can impact the availability and cost of components sourced from China, potentially affecting CyberArk's supply chain. Similarly, sanctions imposed on certain countries by major economies could restrict CyberArk's ability to operate or sell its cybersecurity solutions in those markets, necessitating strategic adjustments to market entry and customer engagement.
Trade agreements, such as those within the European Union or bilateral agreements involving the United States, can create favorable market access for CyberArk, reducing tariffs and simplifying compliance. Conversely, the imposition of new tariffs or the renegotiation of existing trade pacts can increase the cost of doing business and potentially hinder CyberArk's expansion into new territories or its ability to serve existing international client bases. The geopolitical landscape, including regional conflicts, can also disrupt operations and necessitate a re-evaluation of market presence, as seen in potential impacts on Eastern European markets.
The increasing frequency and sophistication of state-sponsored cyberattacks and cyber warfare directly fuel the demand for advanced identity security solutions. As nations and critical infrastructure, like energy grids and financial systems, become prime targets, the imperative for robust defenses against persistent threats grows. For instance, the US Department of Justice reported in 2023 that state-sponsored actors were responsible for a significant portion of the nation's most damaging cyber incidents.
These escalating geopolitical tensions and cyber threats are compelling governments worldwide to strengthen regulatory frameworks and increase cybersecurity budget allocations. In 2024, many countries are revising their national cybersecurity strategies, with significant investments earmarked for protecting critical infrastructure and government networks. This heightened focus translates into greater market opportunities for companies like CyberArk, whose solutions are designed to secure privileged access and protect against advanced persistent threats.
Regulatory Enforcement and Compliance Focus
Governments worldwide are demonstrating increased political will to enforce cybersecurity regulations, driven by a surge in sophisticated cyberattacks. For instance, the European Union's General Data Protection Regulation (GDPR) continues to see robust enforcement, with significant fines levied against non-compliant organizations. Similarly, the California Consumer Privacy Act (CCPA) and its successor, the California Privacy Rights Act (CPRA), are shaping data privacy practices across the United States.
A heightened focus on accountability for data breaches and identity compromise directly benefits companies like CyberArk, as organizations feel greater pressure to invest in robust identity security solutions. This political emphasis translates into increased demand for advanced Privileged Access Management (PAM) and Identity and Access Management (IAM) technologies to meet stricter compliance mandates.
- Increased Regulatory Scrutiny: Expect more stringent audits and penalties for non-compliance with data protection laws like GDPR and CCPA in 2024-2025.
- Data Breach Fines: Companies face substantial financial repercussions, with GDPR fines potentially reaching 4% of global annual revenue, incentivizing proactive security measures.
- Industry-Specific Mandates: Sectors like healthcare and finance are subject to evolving compliance frameworks, requiring specialized identity security solutions.
- Government Cybersecurity Initiatives: National cybersecurity strategies, such as those announced by the US and UK governments, often include provisions that mandate stronger identity and access controls for critical infrastructure.
Government Cloud Adoption and Security Mandates
Government initiatives pushing for cloud migration, such as the US Federal Government's ongoing modernization efforts and the UK's "Cloud First" policy, directly impact CyberArk. These mandates often include stringent security requirements for protecting sensitive data in cloud environments, creating a significant demand for robust identity and access management solutions like those CyberArk offers. For instance, the US federal government's Fiscal Year 2024 budget continued to prioritize IT modernization and cybersecurity, with agencies like the Department of Defense allocating substantial funds towards cloud infrastructure and security enhancements.
Political directives around cloud security, including compliance with standards like FedRAMP in the US, shape procurement processes and dictate the technical capabilities agencies require. CyberArk's ability to meet these specific compliance frameworks and provide secure privileged access management for cloud-based workloads presents a clear opportunity. The increasing adoption of multi-cloud and hybrid cloud strategies by governments worldwide, driven by efficiency and resilience goals, further amplifies the need for unified identity security solutions that can manage diverse cloud environments.
- Increased Demand for Cloud Security: Governments are migrating critical services and data to the cloud, necessitating advanced security for identities and privileged access.
- Compliance-Driven Procurement: Mandates like FedRAMP in the US and similar regulations globally influence the technical specifications and security assurances required from vendors like CyberArk.
- Opportunity in Modernization: Ongoing government IT modernization projects, often involving cloud adoption, create a fertile ground for identity security solutions that support these transitions.
- Focus on Data Protection: Heightened political attention on protecting citizen data in digital services directly translates into a demand for comprehensive identity protection and privileged access controls.
Government cybersecurity policies, such as the EU's NIS2 Directive and the US Cybersecurity Improvement Act of 2023, directly increase demand for robust identity security solutions like CyberArk's. These regulations mandate stronger protections for critical infrastructure and data, compelling organizations to invest in advanced access management. Increased government spending on cybersecurity, with the US allocating an estimated $11.9 billion in FY2024, presents opportunities for companies specializing in privileged access management (PAM).
Geopolitical tensions and state-sponsored cyberattacks, prevalent through 2023 and into early 2024, have elevated cybersecurity to a global national security priority. This has led to expanded budgets and a greater focus on securing digital identities and privileged accounts across both public and private sectors, directly benefiting CyberArk's core offerings.
International trade relations and geopolitical stability significantly impact CyberArk's global operations and market access. For instance, ongoing trade tensions can affect supply chains and the cost of components, while sanctions can restrict market entry, necessitating strategic adjustments to CyberArk's international business approach.
Governments worldwide are increasing cybersecurity budget allocations, with many revising national strategies in 2024 to protect critical infrastructure and networks. This heightened political focus on digital defense creates significant market opportunities for companies like CyberArk, whose solutions are designed to secure privileged access against advanced threats.
What is included in the product
This CyberArk PESTLE analysis examines how political, economic, social, technological, environmental, and legal forces impact the company's operations and strategy.
It provides actionable insights for stakeholders to navigate the external landscape and identify strategic advantages.
CyberArk's PESTLE analysis provides a clear, summarized version of the full analysis for easy referencing during meetings or presentations, simplifying complex external factors into actionable insights.
Economic factors
Global economic growth directly impacts IT budgets, including cybersecurity. As of early 2024, projections for global GDP growth were around 2.9%, a slight slowdown from previous years, indicating a delicate balance. Businesses facing economic uncertainty may scrutinize discretionary IT spending, potentially lengthening sales cycles for new cybersecurity solutions, though the need for essential security remains paramount.
Conversely, periods of economic stability encourage more significant, long-term investments in foundational security infrastructures like identity and access management. For instance, a robust economy in 2023 saw increased enterprise spending on digital transformation initiatives, which often include enhanced cybersecurity as a core component, benefiting companies like CyberArk.
Inflation directly impacts CyberArk's operational expenses. For instance, increased costs for talent acquisition and retention, particularly in specialized cybersecurity roles, can elevate salary budgets. Similarly, the price of cloud infrastructure and software development tools may rise, squeezing profit margins if these costs aren't passed on to customers.
Rising interest rates, as seen with the Federal Reserve's aggressive hikes through 2023 and into 2024, can make it more expensive for CyberArk's enterprise clients to finance significant cybersecurity investments. This could lead to delayed purchasing decisions or a preference for smaller, phased deployments, potentially impacting CyberArk's revenue growth and sales cycles.
These macroeconomic shifts necessitate careful pricing strategies for CyberArk. While higher inflation might justify price increases, the sensitivity of customer budgets to interest rate hikes requires a balanced approach to maintain competitiveness. Furthermore, sustained inflationary pressure and higher borrowing costs could influence the company's own investment decisions in critical areas like research and development for new identity security solutions.
The cybersecurity market is experiencing robust growth, with identity security and privileged access management (PAM) being particularly strong areas. Global cybersecurity spending is projected to reach $267 billion in 2024, and this upward trend is expected to continue, driven by increasing digital adoption and sophisticated cyber threats.
Key industries like finance, healthcare, and government are leading the charge in cybersecurity investments, with North America and Europe representing the largest markets. These sectors are heavily investing in solutions that protect sensitive data and critical infrastructure, aligning well with CyberArk's core offerings.
Ongoing digital transformation initiatives, including cloud migration and remote work adoption, are fundamentally increasing the attack surface for organizations. This surge in interconnectedness directly fuels sustained demand for comprehensive identity protection and PAM solutions to manage and secure privileged access across these expanding digital footprints.
Currency Exchange Rate Volatility
Currency exchange rate volatility significantly impacts CyberArk's global operations. Fluctuations in exchange rates can affect the reported value of international revenue and expenses. For instance, a strengthening U.S. dollar, which has been observed in recent periods, can make CyberArk's software and services more costly for customers in countries with weaker currencies. This could potentially dampen demand in those markets.
Conversely, a strong dollar can also translate into lower operating costs for CyberArk when expenses are incurred in currencies that are weaker relative to the U.S. dollar. This dynamic can provide a cost advantage for the company's international subsidiaries. For example, if CyberArk has significant operational expenses in Europe and the Euro weakens against the dollar, those expenses become cheaper when converted back to U.S. dollars. This can positively impact profit margins on international sales.
- Impact on Revenue: A stronger USD can make CyberArk's offerings more expensive for international clients, potentially slowing sales growth in non-dollar markets.
- Impact on Expenses: Conversely, a weaker foreign currency can reduce the cost of CyberArk's international operations and overhead.
- Hedging Strategies: Companies like CyberArk often employ currency hedging strategies to mitigate the risks associated with significant exchange rate fluctuations.
- Q1 2024 Performance: While specific currency impacts are detailed in quarterly reports, broader economic trends in 2024 suggest continued currency sensitivity for global tech firms.
Competition and Pricing Pressures
The identity security market is experiencing significant competition, with both established cybersecurity giants and nimble startups vying for market share. This intense rivalry directly translates into pricing pressures for companies like CyberArk. For instance, the cybersecurity market as a whole was projected to reach $200 billion in 2024, a figure that intensifies the need for competitive pricing to secure and retain customers.
These pricing pressures can impact CyberArk's profit margins, compelling the company to focus on continuous innovation and differentiation to justify its offerings. Market saturation, where many vendors offer similar solutions, further exacerbates this, potentially devaluing specialized identity security tools. CyberArk must therefore demonstrate clear value and ROI to its clients to navigate these economic headwinds effectively.
- Intense competition from established and emerging players in identity security.
- Pricing pressures impacting profit margins due to market rivalry.
- Need for continuous innovation to maintain market share and perceived value.
- Market saturation and disruptive technologies influencing pricing strategies.
Economic factors significantly shape the cybersecurity landscape for companies like CyberArk. Global economic growth influences IT budgets, with slower growth around 2.9% in early 2024 potentially leading to more cautious spending on non-essential cybersecurity upgrades. Conversely, economic stability typically encourages larger investments in foundational security, such as identity and access management solutions, which CyberArk specializes in.
Inflation and rising interest rates present challenges by increasing operational costs and making financing more expensive for clients, potentially impacting sales cycles. For instance, interest rate hikes through 2023 and into 2024 could prompt customers to opt for phased deployments rather than large upfront investments. Currency fluctuations also play a role, with a strong U.S. dollar making CyberArk's offerings pricier for international customers, though it can also reduce operational costs abroad.
The cybersecurity market itself is a significant economic driver, with global spending projected to reach $267 billion in 2024, fueled by digital transformation and evolving threats. This growth benefits CyberArk, particularly in high-investment sectors like finance and healthcare. However, intense competition within the identity security market creates pricing pressures, requiring CyberArk to focus on innovation and demonstrating clear value to maintain its competitive edge and profit margins.
Preview the Actual Deliverable
CyberArk PESTLE Analysis
The preview you see here is the exact CyberArk PESTLE analysis document you’ll receive after purchase—fully formatted and ready to use.
This comprehensive analysis explores the Political, Economic, Social, Technological, Legal, and Environmental factors impacting CyberArk’s market position. What you’re previewing here is the actual file—fully formatted and professionally structured.
You can trust that the content and structure shown in this preview is the same document you’ll download after payment, offering immediate insights into CyberArk's strategic landscape.
Sociological factors
Growing public and corporate understanding of identity theft and data breaches directly fuels demand for CyberArk's identity security solutions. As more people grasp the value and vulnerability of their digital selves, there's a stronger societal call for robust security. This heightened awareness translates into a greater willingness to invest in advanced protection.
High-profile security incidents, like the widespread ransomware attacks seen throughout 2024, significantly amplify this awareness. These events often serve as stark reminders of cyber risks, influencing both individual caution and organizational purchasing decisions. For instance, the average cost of a data breach in 2024 reached $4.73 million, according to IBM's Cost of a Data Breach Report, underscoring the financial imperative for better security.
The widespread adoption of hybrid and remote work models, accelerated by events in recent years, has fundamentally reshaped the workforce. This shift means organizations must secure access for employees working from anywhere, significantly expanding the potential attack surface. For instance, by early 2024, reports indicated that over 70% of companies were offering some form of remote or hybrid work, a stark contrast to pre-pandemic figures.
This distributed workforce environment creates complex challenges for managing privileged access, as traditional on-premises security perimeters become less relevant. The need for continuous authentication and granular access controls becomes paramount. The increasing reliance on cloud-based applications and services further exacerbates this, demanding robust identity security solutions to protect sensitive data and systems.
Cultural shifts are also at play, with employees expecting more flexibility, which in turn influences how organizations approach security. Companies are increasingly adopting new technologies and adapting their security policies to accommodate these evolving work environments. This necessitates solutions that can seamlessly integrate into diverse IT infrastructures and support a dynamic, often mobile, user base.
The global cybersecurity talent shortage, projected to reach 3.5 million unfilled positions by the end of 2025, directly impacts CyberArk. This scarcity amplifies the demand for CyberArk's identity security solutions, which automate and simplify complex security tasks, making them more accessible for organizations struggling to find skilled personnel.
However, this talent gap also presents a recruitment challenge for CyberArk itself, as it competes for highly specialized professionals to develop and support its offerings. Furthermore, customers may face difficulties in effectively implementing and managing these solutions without adequate in-house expertise, potentially increasing the appeal of managed security services that leverage CyberArk's technology.
Generational Shifts and Digital Natives
Generational shifts, particularly the rise of digitally native individuals, are profoundly impacting how organizations approach cybersecurity. These younger workforces, accustomed to intuitive digital experiences, expect identity and access management (IAM) solutions to be both seamless and highly secure. For CyberArk, this translates into a demand for user-friendly interfaces and robust security that doesn't hinder productivity.
This demographic trend directly influences CyberArk's product development trajectory. As more digitally adept employees enter the professional sphere, there's a growing expectation for security tools that integrate effortlessly with cloud-based applications and mobile devices. This preference will likely drive innovation in areas like passwordless authentication and single sign-on (SSO) solutions that prioritize user experience without compromising on security.
- Digital Natives in the Workforce: By 2025, Gen Z is projected to constitute a significant portion of the global workforce, bringing with them ingrained digital fluency and high expectations for technology integration.
- Demand for User-Friendly Security: Studies indicate that over 60% of employees prefer security solutions that are easy to use, even if it means slightly less robust protection, highlighting a key area for improvement in enterprise security.
- Influence on UI/UX Design: CyberArk's future product design will likely lean towards more streamlined, intuitive interfaces, mirroring the user experience found in popular consumer applications, to cater to this evolving user base.
Trust in Digital Systems and Privacy Expectations
Growing societal trust in digital systems, coupled with heightened privacy expectations, directly impacts the adoption of advanced security technologies. As individuals become more aware of data breaches and surveillance, there's an increasing demand for organizations to implement robust security measures, particularly concerning identity protection. This societal shift amplifies the perceived value and necessity of solutions like those offered by CyberArk, as businesses strive to meet these evolving standards.
The increasing consumer demand for digital privacy and security is a significant driver for businesses to invest in identity security solutions. For instance, a 2024 report indicated that over 70% of consumers are more likely to do business with companies that demonstrate strong data protection practices. This societal pressure directly enhances the perceived value and necessity of CyberArk's offerings, positioning them as critical for maintaining customer trust and regulatory compliance.
- Increased consumer demand for data privacy: A significant portion of the public actively seeks out companies with transparent and secure data handling practices.
- Regulatory scrutiny on data protection: Governments worldwide are enacting stricter data privacy laws, compelling organizations to adopt advanced security measures.
- Impact on brand reputation: Companies perceived as lax on security face significant reputational damage, influencing customer loyalty and market share.
The increasing public awareness of identity theft and data breaches directly fuels demand for CyberArk's identity security solutions. High-profile incidents, such as the widespread ransomware attacks throughout 2024, significantly amplify this awareness, with the average cost of a data breach reaching $4.73 million in 2024. The shift to hybrid and remote work models, with over 70% of companies offering such options by early 2024, expands the attack surface, necessitating robust identity management.
The global cybersecurity talent shortage, projected at 3.5 million unfilled positions by the end of 2025, increases demand for solutions that automate security tasks. Generational shifts, with digitally native individuals expecting seamless and secure IAM solutions, influence CyberArk's product development towards user-friendly interfaces and passwordless authentication.
Societal trust in digital systems and heightened privacy expectations drive the adoption of advanced security. Over 70% of consumers favor companies with strong data protection, directly enhancing the value of CyberArk's offerings for customer trust and compliance.
| Factor | Impact on CyberArk | Supporting Data (2024-2025) |
| Public Awareness of Data Breaches | Increased demand for identity security solutions | Average cost of data breach: $4.73 million (IBM, 2024) |
| Hybrid/Remote Work Adoption | Expanded attack surface, need for secure remote access | Over 70% of companies offer remote/hybrid work (early 2024) |
| Cybersecurity Talent Shortage | Increased demand for automation; recruitment challenges | 3.5 million unfilled cybersecurity positions projected by end of 2025 |
| Digital Natives' Expectations | Demand for user-friendly, integrated security solutions | Gen Z to constitute significant workforce portion by 2025 |
| Consumer Demand for Privacy | Enhanced value of robust data protection practices | Over 70% of consumers prefer companies with strong data protection (2024) |
Technological factors
AI and machine learning are revolutionizing cybersecurity, significantly boosting threat detection and anomaly identification. These technologies enable faster, more accurate identification of suspicious activities that might evade traditional signature-based methods. For instance, in 2024, the global AI in cybersecurity market was valued at approximately $25.3 billion, with projections indicating substantial growth, underscoring its increasing importance.
CyberArk can harness these advancements to elevate its Privileged Access Management (PAM) solutions. By integrating AI, CyberArk can develop more intelligent identity threat detection, pinpointing unusual behavior from privileged accounts. This allows for adaptive access controls, granting or restricting access in real-time based on risk assessments, which is crucial for protecting sensitive assets.
These technological leaps directly influence CyberArk's product roadmap and competitive edge. Companies investing heavily in AI-driven security, like CyberArk, are better positioned to offer proactive and predictive security measures. The ability to offer sophisticated, AI-powered PAM solutions provides a significant differentiator in a crowded cybersecurity market, attracting enterprises seeking advanced protection against sophisticated threats.
The widespread adoption of cloud computing, with a significant portion of enterprise workloads migrating to platforms like AWS, Azure, and Google Cloud, necessitates robust identity security. Many organizations are now embracing multi-cloud strategies to leverage best-of-breed services and avoid vendor lock-in, further complicating security management. CyberArk's strength lies in its ability to provide unified privileged access management (PAM) across these diverse cloud environments, a critical factor for maintaining security and compliance.
The emergence of quantum computing poses a significant long-term threat to current cryptographic standards, which underpin much of today's digital security and identity protection. As quantum computers advance, their ability to solve complex mathematical problems could render widely used encryption algorithms obsolete, potentially compromising sensitive data and access controls.
This technological shift necessitates a proactive approach to developing and implementing quantum-resistant cryptography. CyberArk, as a leader in identity security, will likely need to invest in research and development to integrate these new cryptographic methods into its platform, ensuring the continued robustness of its identity and access management solutions against future threats.
DevOps and Automation Trends
The rapid expansion of DevOps and automation is fundamentally reshaping identity security. As organizations increasingly rely on automated processes and machine-to-machine communication, the sheer volume of non-human identities requiring protection is surging. This shift necessitates advanced Privileged Access Management (PAM) solutions capable of managing and securing these dynamic, ephemeral identities.
CyberArk's strategic advantage lies in its robust capabilities to secure these machine identities and seamlessly integrate with the automation tools that underpin modern DevOps workflows. For instance, by 2025, it's projected that over 50% of enterprise workloads will be managed through automated CI/CD pipelines, highlighting the critical need for PAM solutions that can provision, de-provision, and monitor access for these automated systems. This integration is paramount for maintaining a strong security posture in highly dynamic IT environments.
- Increased Machine Identities: The adoption of CI/CD pipelines, containers, and APIs is leading to an exponential growth in machine identities, demanding specialized PAM solutions.
- Automation Integration: CyberArk's ability to integrate with automation tools is crucial for securing the entire lifecycle of automated processes, from development to deployment.
- Security in Dynamic Environments: By 2025, over 50% of enterprise workloads are expected to be managed via automated CI/CD pipelines, underscoring the need for PAM that can handle this velocity and complexity.
Cybersecurity Mesh Architecture and Zero Trust
The increasing adoption of cybersecurity mesh architecture and Zero Trust principles, centered on the 'never trust, always verify' philosophy and distributed security controls, directly benefits CyberArk. These architectural shifts reinforce CyberArk's identity-centric security model, making its Privileged Access Management (PAM) solutions essential building blocks.
These frameworks significantly boost the demand for integrated identity and access management (IAM) solutions. For instance, Gartner predicted that by 2025, 70% of new remote access solutions would be integrated into platform-as-a-service (PaaS) offerings, up from 15% in 2020, highlighting the shift towards centralized, identity-aware security.
- Growing Zero Trust Adoption: Organizations are increasingly implementing Zero Trust frameworks to mitigate sophisticated cyber threats.
- Mesh Architecture Benefits: Cybersecurity mesh architecture allows for more flexible and granular security policies, crucial for distributed workforces.
- Identity as the Core: Both trends underscore the critical role of identity as the new security perimeter, aligning perfectly with CyberArk's core offerings.
- Market Growth: The global identity and access management market is projected to reach $31.4 billion by 2026, indicating strong demand for solutions like CyberArk's.
AI and machine learning are transforming cybersecurity, enhancing threat detection with advanced anomaly identification capabilities. The global AI in cybersecurity market reached approximately $25.3 billion in 2024, showcasing significant growth and its increasing importance in the sector.
CyberArk can leverage these AI advancements to improve its Privileged Access Management (PAM) solutions, enabling more intelligent identity threat detection and adaptive access controls. This integration is crucial for protecting sensitive assets by pinpointing unusual privileged account behavior.
The increasing reliance on cloud computing, including multi-cloud strategies, necessitates robust identity security. CyberArk's ability to provide unified PAM across diverse cloud environments is a key strength, addressing the complexities of modern IT infrastructure.
The rise of DevOps and automation is driving a surge in machine identities, requiring advanced PAM solutions. By 2025, over 50% of enterprise workloads are expected to be managed through automated CI/CD pipelines, highlighting the critical need for PAM to secure these dynamic systems.
Legal factors
Evolving global data protection laws like GDPR and CCPA significantly impact CyberArk by increasing demand for its privileged access management solutions. These regulations, which impose strict controls on personal data access, make CyberArk's offerings crucial for businesses aiming to avoid hefty fines for non-compliance. For instance, GDPR fines can reach up to 4% of global annual turnover or €20 million, whichever is higher, underscoring the critical need for robust identity and access management.
Industry-specific compliance mandates are a significant driver for CyberArk's business. Regulations like HIPAA in healthcare, PCI DSS for payment card data, and NERC CIP for energy infrastructure all impose strict rules on how sensitive data and privileged access are managed. These rules directly necessitate robust identity and access management solutions, making CyberArk's offerings essential for companies in these sectors to avoid hefty fines and reputational damage.
Governments worldwide are enacting stricter cybersecurity incident reporting laws. For instance, the EU's NIS2 Directive, effective in early 2024, mandates timely reporting of significant cyber incidents for a broader range of entities. This legal pressure directly increases demand for solutions like CyberArk's, as organizations must demonstrate compliance and mitigate risks associated with failing to report promptly.
These regulations, such as California's CCPA/CPRA and various sector-specific rules, impose significant penalties for non-compliance and data breaches. The financial implications of fines, reputational damage, and operational disruption compel businesses to invest more heavily in proactive security measures, including identity and access management, to prevent incidents that trigger these reporting obligations.
Software Licensing and Intellectual Property Laws
CyberArk operates within a stringent legal environment governed by software licensing and intellectual property (IP) laws. Protecting its core technologies, particularly its privileged access management solutions, through patents and copyrights is paramount. In 2024, the global software market continued to see robust growth, underscoring the value of IP in this sector. Failure to adequately protect its innovations or respect third-party IP could lead to costly litigation and damage its market standing.
The company must ensure strict compliance with its own software licensing agreements and those of its partners and customers. Legal disputes, such as patent infringement claims, pose a significant risk, potentially impacting CyberArk's competitive advantage and financial performance. For instance, the US Patent and Trademark Office granted numerous software-related patents in 2024, highlighting the active landscape of IP protection in the tech industry.
- Patent Portfolio Strength: CyberArk's ability to secure and defend patents for its unique identity security solutions is a key legal factor.
- License Compliance: Adherence to all software licensing terms, both for its own products and any third-party components used, is critical for operational continuity.
- IP Litigation Risk: The potential for legal challenges from competitors or other entities regarding intellectual property can disrupt business and incur significant legal costs.
- Global IP Enforcement: Enforcing IP rights across various international jurisdictions presents complex legal hurdles and requires strategic management.
Government Procurement Regulations and Standards
Government procurement of cybersecurity solutions is heavily regulated, with stringent legal frameworks dictating compliance. These regulations often mandate specific security certifications, such as FedRAMP in the United States, which CyberArk has achieved for certain offerings, demonstrating adherence to rigorous government security standards.
Data residency requirements are also paramount, compelling vendors to store and process sensitive government data within specific geographical boundaries. Furthermore, supply chain integrity is a critical legal and operational concern, requiring thorough vetting of all components and partners involved in delivering cybersecurity solutions. CyberArk's commitment to these standards is essential for accessing the substantial public sector market, which represents a significant revenue opportunity.
- FedRAMP Authorization: CyberArk has achieved FedRAMP authorization, a key legal requirement for U.S. federal agencies procuring cloud-based cybersecurity solutions.
- Data Residency Compliance: Meeting diverse data residency laws across different jurisdictions is crucial for global government contracts.
- Supply Chain Security Mandates: Adherence to strict supply chain security standards, like those outlined in NIST SP 800-161, is vital for government trust.
Increasingly stringent global data protection laws, such as the EU's GDPR and California's CCPA/CPRA, directly boost demand for CyberArk's privileged access management solutions. Non-compliance penalties, like GDPR fines potentially reaching 4% of global annual turnover, incentivize robust security investments. Furthermore, evolving cybersecurity incident reporting mandates, like the EU's NIS2 Directive effective in early 2024, compel organizations to implement comprehensive security measures, further benefiting CyberArk.
CyberArk's business is significantly influenced by industry-specific compliance requirements, including HIPAA for healthcare and PCI DSS for payment card data. These regulations necessitate strong identity and access management, making CyberArk's services essential for companies in regulated sectors to avoid substantial fines and reputational damage. The global cybersecurity market continued its upward trajectory in 2024, highlighting the critical role of compliance-driven solutions.
Intellectual property laws are paramount for CyberArk, requiring diligent protection of its core technologies through patents and copyrights. The company must navigate complex licensing agreements and mitigate the risk of IP litigation, which could impact its competitive edge. The active landscape of software patent grants in 2024 underscores the importance of a strong IP strategy.
| Legal Factor | Impact on CyberArk | Example/Data Point |
| Data Protection Laws (GDPR, CCPA) | Increased demand for PAM solutions | GDPR fines up to 4% of global annual turnover |
| Industry-Specific Compliance (HIPAA, PCI DSS) | Necessity for robust IAM | Critical for avoiding fines and reputational damage |
| Cybersecurity Incident Reporting | Drives adoption of security measures | EU NIS2 Directive (early 2024) mandates timely reporting |
| Intellectual Property Protection | Essential for competitive advantage | Active software patent grants in 2024 |
Environmental factors
Data centers and the IT infrastructure they house are facing increasing scrutiny for their energy consumption. This includes the significant power required to run cybersecurity solutions like those offered by CyberArk. While CyberArk's software is efficient, the overall footprint of the systems it secures contributes to environmental concerns.
A growing societal demand for green IT practices is influencing customer choices. Businesses are actively seeking more energy-efficient solutions and are increasingly migrating to cloud-based deployments, which often promise better energy management. This trend could shape preferences for cybersecurity vendors who demonstrate a commitment to sustainability and offer solutions that align with these green IT goals.
Globally, data centers are estimated to consume between 1% and 5% of the world's electricity, a figure expected to rise with increasing digital transformation. For instance, in 2023, the International Energy Agency reported that global electricity demand from data centers, crypto mining, and transmission grew by about 10%. This highlights the critical need for cybersecurity providers to consider the energy efficiency of their offerings and the infrastructure they protect.
The technology sector is facing heightened scrutiny regarding environmental sustainability and ethical conduct throughout its supply chains. Even software firms like CyberArk, while not directly manufacturing hardware, depend on physical components and cloud infrastructure providers.
Customers and investors are increasingly demanding clear information about the environmental impact and ethical sourcing of these partners. For instance, by 2025, many large enterprises will have robust supplier ESG (Environmental, Social, and Governance) reporting requirements, impacting their entire technology stack.
This growing emphasis directly influences CyberArk's vendor selection processes and shapes its broader corporate social responsibility initiatives, pushing for greater transparency and accountability from its upstream partners.
The IT industry's contribution to electronic waste (e-waste) is a growing concern, and while CyberArk focuses on software, its solutions are embedded within hardware that eventually becomes obsolete. Globally, e-waste generation reached an estimated 62 million metric tons in 2020 and is projected to increase significantly by 2027.
A growing emphasis on circular economy principles, aiming to minimize waste and maximize resource utilization, is influencing customer purchasing decisions. Businesses are increasingly looking for partners who demonstrate a commitment to sustainable IT practices, potentially favoring cloud-based solutions that reduce the need for physical infrastructure and its associated lifecycle impacts.
Climate Change Impact on Business Operations
Climate change poses a growing threat to business operations, including those of companies like CyberArk. Extreme weather events, such as floods, hurricanes, and wildfires, can severely disrupt critical infrastructure, including data centers and communication networks. This disruption can impact CyberArk's ability to deliver its services and, more importantly, affect its customers' capacity to maintain business continuity and secure their digital assets.
The resilience and disaster recovery planning for digital systems are directly influenced by environmental factors. CyberArk's solutions, which focus on identity security and privileged access management, play a crucial role in ensuring that organizations can recover and operate securely even when facing physical infrastructure challenges stemming from climate change. For instance, the increasing frequency of severe weather events in 2024 and projections for 2025 highlight the need for robust, geographically dispersed IT infrastructure and secure remote access capabilities.
The broader risk landscape is also shaped by environmental changes, creating new challenges for cybersecurity. As climate change intensifies, the potential for cascading failures across interconnected systems grows. This means that even indirect environmental impacts can necessitate stronger cybersecurity measures to protect against threats that exploit vulnerabilities exposed by climate-related disruptions. Organizations are increasingly factoring climate risk into their overall business continuity and cybersecurity strategies.
- Increased frequency of extreme weather events globally in 2024, leading to significant infrastructure damage.
- The World Economic Forum's Global Risks Report 2024 identified extreme weather and climate action failure as top long-term risks.
- Cybersecurity spending is projected to reach over $200 billion globally by 2025, partly driven by the need to secure operations against a wider range of threats, including those exacerbated by climate events.
- CyberArk's focus on secure remote access and identity protection becomes even more critical for maintaining operational resilience during climate-induced disruptions.
Corporate Social Responsibility (CSR) and ESG Reporting
The focus on Corporate Social Responsibility (CSR) and Environmental, Social, and Governance (ESG) reporting is a significant trend for publicly traded companies, including CyberArk. Investors and stakeholders are increasingly scrutinizing companies not just on financial performance but also on their environmental impact and ethical operations. This shift means that a company's commitment to sustainability and responsible business practices directly influences its brand image and its ability to attract capital from environmentally conscious investors.
For CyberArk, demonstrating a strong ESG framework can translate into tangible benefits. For instance, in 2023, the global ESG investing market was estimated to be over $37 trillion, highlighting the substantial capital pool available for companies with robust sustainability credentials. By integrating ESG principles into its core strategy, CyberArk can enhance its brand reputation, potentially leading to improved investor relations and a more resilient long-term valuation.
- Growing Investor Demand: A significant portion of institutional investors now incorporate ESG factors into their investment decisions, seeking companies with strong environmental stewardship and social responsibility.
- Brand Reputation Enhancement: Proactive CSR and ESG initiatives can bolster CyberArk's public image, differentiating it from competitors and fostering trust among customers and partners.
- Attracting Sustainable Capital: Companies with clear ESG commitments are better positioned to attract capital from a growing segment of investors prioritizing sustainable and ethical business practices.
The increasing energy consumption of data centers and IT infrastructure presents an environmental challenge, impacting the operational footprint of cybersecurity solutions like CyberArk's. Growing demand for green IT practices is pushing businesses towards energy-efficient solutions and cloud migration, influencing customer preferences for sustainable cybersecurity vendors.
The IT sector faces scrutiny over e-waste, with global generation projected to rise significantly by 2027, impacting hardware lifecycles where CyberArk's software is deployed. Circular economy principles are gaining traction, favoring partners committed to sustainable IT and potentially cloud solutions that minimize physical infrastructure impacts.
Climate change poses risks to critical IT infrastructure, with extreme weather events in 2024 and projections for 2025 highlighting the need for resilient, secure systems. CyberArk's identity security solutions are vital for business continuity during climate-induced disruptions, with cybersecurity spending expected to exceed $200 billion globally by 2025, partly due to these evolving threats.
| Environmental Factor | Impact on CyberArk | Relevant Data/Projections |
|---|---|---|
| Data Center Energy Consumption | Increased scrutiny on the energy footprint of IT infrastructure secured by CyberArk. | Data centers consume 1-5% of global electricity; IEA reported a 10% growth in demand from data centers in 2023. |
| Green IT Demand | Customer preference shift towards energy-efficient and cloud-based cybersecurity solutions. | Businesses actively seek vendors demonstrating sustainability and offering green IT-aligned solutions. |
| E-waste | Lifecycle impact of hardware hosting CyberArk's software. | Global e-waste reached 62 million metric tons in 2020 and is projected to increase significantly by 2027. |
| Climate Change & Extreme Weather | Disruption of critical IT infrastructure, necessitating robust business continuity and cybersecurity. | Increased frequency of severe weather events in 2024; WEF Global Risks Report 2024 identifies extreme weather as a top long-term risk. |
PESTLE Analysis Data Sources
Our CyberArk PESTLE Analysis is built on a comprehensive review of data from government cybersecurity mandates, industry analyst reports, and global technology adoption trends. We integrate insights from regulatory bodies, economic forecasts, and legal frameworks to ensure a holistic understanding of the external landscape.
