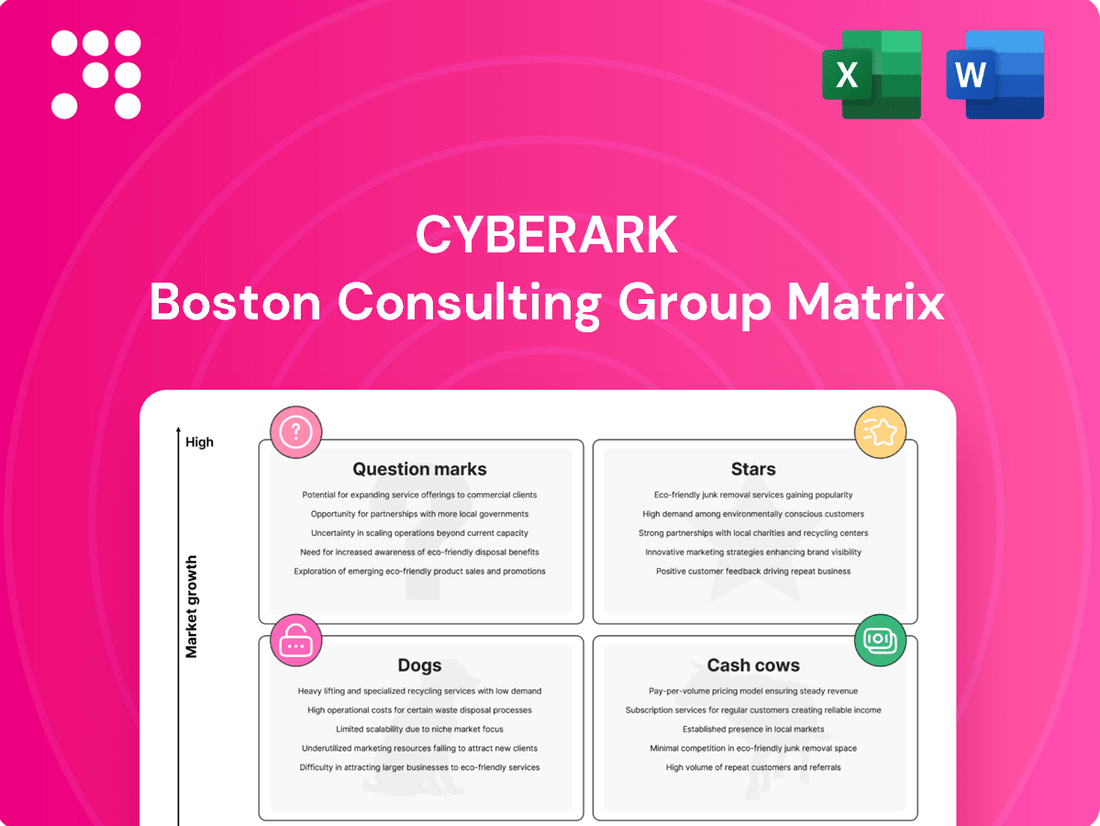
CyberArk Boston Consulting Group Matrix
Fully Editable
Tailor To Your Needs In Excel Or Sheets
Professional Design
Trusted, Industry-Standard Templates
Pre-Built
For Quick And Efficient Use
No Expertise Is Needed
Easy To Follow
CyberArk Bundle
CyberArk's strategic positioning is illuminated by its BCG Matrix, offering a clear visual of its product portfolio's market share and growth potential. Understand which solutions are driving growth, which are stable income generators, and which require careful evaluation.
This preview is just the beginning. Get the full BCG Matrix report to uncover detailed quadrant placements, data-backed recommendations, and a roadmap to smart investment and product decisions for CyberArk's offerings.
Stars
CyberArk's Secure AI Agents Solution, now available on AWS Marketplace, taps into a burgeoning market driven by the widespread adoption of AI. This offering addresses the escalating demand for robust security controls specifically designed for the privileged access of these AI agents, a critical need as their capabilities expand.
The rapid proliferation of AI agents creates a significant new attack surface, and CyberArk's solution directly leverages its established strengths in identity security to protect this emerging threat vector. This strategic move allows CyberArk to capitalize on its core competencies while catering to a critical, high-growth segment of the cybersecurity landscape.
CyberArk's acquisition of Venafi in October 2024 dramatically expanded its machine identity security offerings. This move positions CyberArk to capitalize on the rapidly growing market for managing machine identities, which are now vastly more numerous than human identities. The integration allows CyberArk to provide comprehensive protection for certificates, Public Key Infrastructure (PKI), and workload identities, key components in securing modern IT environments.
CyberArk Cloud Entitlements Manager is positioned as a strong contender in the cloud security market, leveraging AI to tackle the complex issue of misconfigured cloud permissions. This is a high-growth area, with organizations increasingly adopting cloud technologies, creating a significant demand for solutions that can manage and secure cloud identities and access.
The cloud security market is experiencing rapid expansion. For instance, the global cloud security market size was valued at approximately USD 15.1 billion in 2023 and is projected to grow at a compound annual growth rate (CAGR) of around 16.5% from 2024 to 2030, reaching an estimated USD 43.7 billion by 2030. CyberArk's offering directly addresses a critical pain point within this burgeoning market, making it a strategic product.
Just-in-Time (JIT) Access and Zero Standing Privileges (ZSP)
CyberArk's emphasis on Just-in-Time (JIT) access and Zero Standing Privileges (ZSP) is a key driver in its Privileged Access Management (PAM) strategy, positioning it strongly in a high-growth security market. This approach directly addresses the need to minimize the attack surface by ensuring privileged access is granted only when needed and for a limited duration.
The market for PAM solutions, which includes JIT and ZSP capabilities, is experiencing robust expansion. For instance, the global PAM market was valued at approximately $4.5 billion in 2023 and is projected to reach over $11 billion by 2028, demonstrating a compound annual growth rate (CAGR) of around 20%. This growth underscores the increasing adoption of these advanced security principles by organizations worldwide.
- JIT Access: Grants temporary, context-aware access to sensitive systems, significantly reducing the window of vulnerability.
- ZSP: Eliminates persistent, standing privileged accounts, ensuring that no elevated access exists by default.
- Market Growth: The PAM market, a key area for JIT/ZSP, is expected to grow substantially, reflecting strong demand for these security measures.
- Security Posture: These capabilities are central to modern cybersecurity frameworks, helping organizations comply with regulations and defend against sophisticated threats.
Developer and Cloud Workload Security
CyberArk's focus on developer and cloud workload security addresses a critical need in today's technology landscape. As organizations increasingly adopt cloud-native architectures and DevOps practices, securing the identities and access of developers and the workloads themselves becomes paramount. This segment is experiencing rapid growth, with the global cloud security market projected to reach $150 billion by 2025, highlighting the immense opportunity.
CyberArk's solutions are tailored to integrate security directly into the development lifecycle. This includes managing secrets, such as API keys and credentials, within DevOps pipelines, preventing them from being hardcoded or exposed. By embedding security early, they empower developers to build and deploy applications more securely and efficiently. In 2024, organizations are prioritizing DevSecOps, with a significant percentage of companies implementing automated security testing in their CI/CD pipelines.
The company's offerings for cloud workload identities are equally vital. This involves securing machine identities, like those used by containers and serverless functions, which are essential for communication and access in cloud environments. CyberArk's approach ensures that these dynamic identities are managed and protected, reducing the attack surface. The adoption of cloud workloads continues to surge, with reports indicating that over 90% of enterprises are now using at least one cloud service.
These specialized identity security capabilities position CyberArk to capitalize on the high-growth demand in these markets. By providing robust security for developers and cloud workloads, CyberArk is enabling organizations to accelerate innovation while maintaining a strong security posture.
- Developer Access Security: Protecting privileged access for developers working with sensitive code repositories and infrastructure.
- DevOps Secrets Management: Ensuring secure handling of credentials and secrets within automated build and deployment pipelines.
- Cloud Workload Identity Security: Securing the identities of cloud-based applications, containers, and services to prevent unauthorized access.
- Market Growth: Capitalizing on the expanding cloud-native and DevSecOps markets, driven by digital transformation initiatives.
CyberArk's Secure AI Agents solution is a prime example of a "Star" in the BCG matrix, addressing a rapidly expanding market with high growth potential. By securing the privileged access of AI agents, CyberArk is tapping into a critical need as AI adoption accelerates across industries, creating new attack vectors.
The company's acquisition of Venafi in late 2024 significantly bolsters its machine identity security, another "Star" area. This positions CyberArk to manage the exponentially growing number of machine identities, crucial for securing modern, interconnected environments.
CyberArk's Cloud Entitlements Manager is also a "Star," leveraging AI to address cloud misconfigurations. With the cloud security market projected to reach $43.7 billion by 2030, this offering is well-placed to capture significant market share.
The company's core Privileged Access Management (PAM) capabilities, including Just-in-Time access and Zero Standing Privileges, continue to perform as "Stars." The PAM market is set to exceed $11 billion by 2028, driven by demand for robust security principles.
| Product/Solution | BCG Category | Market Growth | CyberArk's Position |
|---|---|---|---|
| Secure AI Agents | Star | High (AI adoption) | Addresses critical security need for AI agents |
| Machine Identity Security (post-Venafi) | Star | High (exponential growth of machine identities) | Comprehensive protection for certificates, PKI, workload identities |
| Cloud Entitlements Manager | Star | High (cloud security market growth) | AI-driven solution for cloud misconfigurations |
| PAM (JIT/ZSP) | Star | High (PAM market growth) | Core strength, minimizes attack surface |
What is included in the product
This BCG Matrix analysis provides a strategic overview of CyberArk's product portfolio, categorizing each offering as a Star, Cash Cow, Question Mark, or Dog to guide investment decisions.
CyberArk's BCG Matrix analysis offers a clear, actionable roadmap by categorizing privileged access solutions, relieving the pain of resource allocation uncertainty.
Cash Cows
CyberArk's core Privileged Access Management (PAM) suite, featuring solutions like Privileged Session Manager (PSM) and Enterprise Password Vault (EPV), firmly positions it as a cash cow. These offerings are the bedrock of CyberArk's business, dominating a mature but critical cybersecurity market. Their widespread adoption by large enterprises and essential infrastructure providers ensures a steady and substantial revenue stream.
CyberArk's self-hosted Secrets Manager, while facing competition from cloud-native solutions, remains a significant revenue generator. Organizations prioritizing on-premises control for critical credentials continue to rely on this offering, ensuring a stable installed base.
This segment is characterized by recurring revenue streams, bolstered by long-term customer commitments and the essential nature of robust security infrastructure. Its "cash cow" status is further solidified by the high switching costs associated with foundational security platforms.
In 2023, CyberArk reported that its Identity Security platform, which includes Secrets Management, saw substantial growth, with a notable portion of revenue stemming from its established on-premises customer base. This highlights the enduring value of their self-hosted solutions.
CyberArk's Endpoint Privilege Manager (EPM) is a prime example of a cash cow within the cybersecurity landscape, particularly in the realm of privilege management. Its established market presence in controlling endpoint privileges, a critical and enduring security concern, ensures a steady stream of revenue. This is driven by the continuous need for organizations to comply with regulatory mandates and the ever-present risk associated with excessive local administrator rights.
The predictable demand for EPM stems from its role in mitigating significant security threats, making it a recurring investment for businesses. As of 2024, the global endpoint security market, which EPM significantly contributes to, is projected to reach over $20 billion, indicating the substantial and consistent demand for such solutions. CyberArk's strong positioning in this segment allows EPM to generate reliable and substantial profits.
Workforce Access Management (SSO/MFA)
CyberArk's workforce access management solutions, encompassing Single Sign-On (SSO) and Multi-Factor Authentication (MFA), represent a core offering with a substantial and loyal customer base. These foundational identity security tools provide a consistent and reliable revenue stream, underscoring their position as a cash cow within the company's portfolio.
While the market for basic SSO and MFA is mature and highly competitive, CyberArk leverages its strong brand reputation and integrated platform to maintain its market share. This stability is crucial for funding innovation in other, higher-growth areas of the business.
- Established Market Presence: CyberArk's SSO and MFA solutions are widely adopted, serving as essential components of many organizations' cybersecurity infrastructure.
- Predictable Revenue Generation: These mature products contribute stable and predictable revenue, acting as a financial anchor for the company.
- Competitive Landscape: The SSO/MFA market is crowded, demanding continuous investment in feature enhancements and customer support to retain market leadership.
- Foundation for Growth: The consistent cash flow from these offerings enables CyberArk to invest in developing and acquiring cutting-edge solutions for emerging cybersecurity threats.
Maintenance and Professional Services for Established Products
Maintenance and professional services for CyberArk's established Privileged Access Management (PAM) and related solutions represent a core cash cow. This recurring revenue stream is vital, as customers depend on these services to ensure ongoing compliance and to fine-tune their existing CyberArk deployments. For instance, in 2023, CyberArk reported that its recurring revenue, which heavily includes maintenance and support, grew significantly, underscoring the stability of this segment.
These services are critical for maintaining the operational integrity and security posture of customer environments. This creates a predictable and consistent income for CyberArk, as customers renew contracts to benefit from ongoing support, updates, and expert assistance. This segment consistently contributes to profitability, allowing CyberArk to invest in its growth areas.
- Recurring Revenue: Maintenance contracts provide a predictable income.
- Customer Reliance: Services are essential for compliance and optimization.
- Stability: This segment offers a reliable income stream for the company.
- 2023 Performance: CyberArk saw substantial growth in its recurring revenue.
CyberArk's core Privileged Access Management (PAM) suite, including solutions like Privileged Session Manager and Enterprise Password Vault, acts as a significant cash cow. These offerings are foundational to its business, serving a mature but essential cybersecurity market with widespread enterprise adoption, ensuring a consistent and substantial revenue stream.
The company's self-hosted Secrets Manager, despite growing competition from cloud-native alternatives, continues to be a strong revenue generator. Organizations prioritizing on-premises control for sensitive credentials maintain reliance on this offering, solidifying its stable installed base and predictable income.
CyberArk's Endpoint Privilege Manager (EPM) is another key cash cow. Its established presence in controlling endpoint privileges, a critical and enduring security need, guarantees a steady revenue flow driven by regulatory compliance and the ongoing risk of excessive local administrator rights.
The workforce access management solutions, such as Single Sign-On (SSO) and Multi-Factor Authentication (MFA), also function as cash cows. These mature identity security tools provide a stable and reliable revenue stream, leveraging CyberArk's strong brand to maintain market share and fund innovation in other areas.
| Solution Area | BCG Matrix Category | Key Characteristics | Revenue Contribution | Market Outlook |
| Core PAM Suite | Cash Cow | Mature market, high adoption, essential security | Substantial and steady | Stable, ongoing demand |
| Self-Hosted Secrets Manager | Cash Cow | On-premises control preference, stable installed base | Significant | Continued need for on-prem solutions |
| Endpoint Privilege Manager (EPM) | Cash Cow | Critical security need, regulatory compliance | Steady | Growing endpoint security market (projected >$20B in 2024) |
| SSO & MFA Solutions | Cash Cow | Foundational identity security, loyal customer base | Consistent and reliable | Mature but stable, competitive |
Preview = Final Product
CyberArk BCG Matrix
The CyberArk BCG Matrix preview you are viewing is the identical, fully polished document you will receive immediately after your purchase. This means no watermarks, no placeholder text, and no altered content—just the complete, professionally formatted strategic analysis ready for immediate deployment in your business planning.
Dogs
CyberArk's legacy perpetual license revenue is a clear indicator of its strategic shift towards a subscription-based Software-as-a-Service (SaaS) model. This segment represents a declining, low-growth area, reflecting minimal ongoing strategic investment as the company prioritizes its recurring revenue streams.
As of the first quarter of 2024, CyberArk reported that subscription revenue represented a significant majority of its overall sales, further underscoring the diminishing importance of perpetual licenses. This legacy business line is generating reduced returns and is actively being phased out to focus resources on the more scalable and predictable SaaS offerings.
Outdated on-premises deployment models for certain cybersecurity solutions, while still supported for some existing clients, are increasingly being viewed as dogs in the current market. This is largely due to the rapid industry-wide shift towards more flexible cloud and hybrid architectures.
These legacy on-premises setups often demand significant manual administration and lack the inherent agility of modern, cloud-native alternatives. For instance, the global cloud computing market is projected to reach $1.3 trillion by 2025, highlighting the strong market preference for cloud-based solutions over traditional on-premises infrastructure.
Niche or discontinued standalone products within CyberArk's portfolio, such as older versions of Privileged Access Security (PAS) or specific identity management tools no longer actively developed, likely represent the 'Dogs' category. These offerings might still cater to a limited, legacy customer base, demanding ongoing support and maintenance without contributing significantly to new market growth or platform integration.
Products in this 'Dog' quadrant typically exhibit low market share and minimal growth potential. For instance, if CyberArk had a standalone endpoint privilege management solution launched pre-2020 that has since been superseded by its integrated Identity Security platform, it would fit this description. Such products can strain resources disproportionately, as seen in the cybersecurity sector where maintaining support for outdated, specialized solutions can divert engineering and customer success efforts from more strategic, high-growth areas.
Solutions with Limited Integration Capabilities
Products in this category, often older versions or specific features, struggle to connect with today's cloud-native architectures, DevOps pipelines, and broader security frameworks. This limited integration capability hinders their adoption in modern IT environments.
These offerings face challenges in capturing new market share as businesses increasingly demand unified and interoperable security solutions. Companies are prioritizing platforms that can seamlessly connect and automate security processes across their entire digital footprint.
- Limited Cloud and DevOps Connectivity: Many legacy solutions were not designed for cloud or containerized environments, leading to integration gaps.
- Stagnant Market Share Growth: Lack of modern integration capabilities makes these products less appealing to new customers seeking comprehensive security platforms.
- Potential for Customer Burden: As customers upgrade their infrastructure, these non-integrated solutions can become maintenance burdens and security risks.
- Focus on Modernization or Divestiture: Companies with such offerings often need to invest in updating them or consider divesting them to focus on more integrated solutions.
Highly Manual Identity Governance Processes
CyberArk's identity governance, particularly in areas where processes remain highly manual, falls into the Dogs quadrant of the BCG matrix. These manual aspects, often seen in legacy client implementations, represent a segment with low growth potential and efficiency. For instance, the continued reliance on manual access reviews or onboarding processes can lead to significant time expenditure and increased risk of errors.
The acquisition of Zilla Security by CyberArk in 2023, for an undisclosed sum, directly targets these inefficiencies. Zilla's platform is designed to automate and streamline identity and access management (IAM) workflows, including the modernization of these manual governance tasks. This strategic move aims to transform a lower-performing segment of CyberArk's portfolio into a more efficient and potentially higher-growth area by leveraging automation.
- Manual Access Reviews: Many organizations still conduct periodic access reviews manually, which is time-consuming and prone to oversight.
- Onboarding/Offboarding Inefficiencies: Inconsistent or manual processes for granting and revoking access during employee onboarding and offboarding create security gaps.
- Compliance Reporting: Generating compliance reports often involves manual data aggregation, increasing the risk of inaccuracies.
- Zilla's Automation Focus: Zilla Security's technology is geared towards automating these very processes, reducing manual effort and improving accuracy.
CyberArk's legacy perpetual license revenue and outdated on-premises solutions are prime examples of its 'Dogs' in the BCG matrix. These segments represent low-growth, low-market-share areas that are being phased out to focus on the company's subscription-based SaaS model. The acquisition of Zilla Security in 2023 aims to address inefficiencies in manual identity governance processes, transforming a potential 'Dog' into a more automated and efficient offering.
Question Marks
CyberArk's acquisition of Zilla Security in February 2025 positions it to bolster its Identity Governance and Administration (IGA) offerings, a sector experiencing robust growth. This move targets a market where established competitors currently hold substantial sway, indicating a strategic push for CyberArk to gain a stronger foothold.
The integration of Zilla Security represents a significant investment for CyberArk in a market segment where it's still building its presence. The success of this venture will hinge on CyberArk's ability to effectively leverage Zilla's technology and capture meaningful market share in the competitive IGA landscape.
CyberArk's Secure Cloud Access (SCA) MCP Server and Agent Guard, available on AWS Marketplace, directly address the rapidly expanding need to secure AI agents and cloud environments. This market is experiencing significant growth, with cloud security spending projected to reach $140 billion by 2025, according to Gartner. While CyberArk has strong existing credentials in identity security, these new offerings represent a strategic push into a high-potential, yet still developing, segment where establishing dominance will require focused investment.
The success of SCA MCP Server and Agent Guard hinges on robust marketing and sales initiatives to capitalize on this emerging opportunity. Industry reports from 2024 indicate that organizations are increasingly prioritizing AI security, with over 60% of companies planning to increase their AI security budgets. CyberArk's ability to effectively communicate the value proposition of these tools and drive adoption will be crucial in translating their technological capabilities into substantial market share gains in this competitive landscape.
CyberArk is leveraging AI to significantly boost its security analytics and threat detection capabilities, positioning itself for substantial growth in the cybersecurity market. This integration aims to provide deeper, risk-based insights, moving beyond traditional security measures.
While these AI-driven analytics represent a high-growth trajectory for CyberArk, they are still in a developmental phase, with market adoption gradually increasing. This contrasts with their established and mature Privileged Access Management (PAM) solutions, which currently form the bedrock of their offerings.
Expanded Machine Identity Management Beyond PKI (Post-Venafi Integration)
While Venafi's acquisition bolstered CyberArk's Public Key Infrastructure (PKI) capabilities, the real growth opportunity lies in managing a wider array of machine identities. This includes dynamic entities like containers, Internet of Things (IoT) devices, and serverless functions, which often rely on methods beyond traditional certificates.
CyberArk must strategically invest in expanding its platform to address these evolving non-human identities. This is crucial for capturing market share in a rapidly growing segment of the cybersecurity landscape. For instance, the global machine identity management market is projected to reach $1.5 billion by 2027, with non-PKI solutions showing significant acceleration.
- Expanding Scope: Moving beyond certificates to manage identities for containers, IoT, and serverless functions is a key growth area.
- Market Potential: The non-PKI machine identity management segment is experiencing rapid expansion, representing a substantial revenue opportunity.
- Investment Focus: CyberArk needs to prioritize platform development to effectively address this broader range of machine identities.
- Competitive Advantage: Early and comprehensive investment in this area will solidify CyberArk's leadership in the evolving machine identity management space.
Solutions for Managed Service Providers (MSPs)
CyberArk's strategic focus on Managed Service Providers (MSPs) is evident through its enhanced console and new partner programs, signaling a significant opportunity to deliver identity security as a service. This move taps into a high-growth market where MSPs are increasingly sought after for specialized cybersecurity solutions.
To capture substantial market share within the MSP channel, CyberArk needs to implement channel-specific strategies. This includes robust investment in building and nurturing partnerships, alongside dedicated support structures designed to meet the unique operational and sales needs of MSPs.
- Market Entry Strategy: CyberArk is actively expanding its MSP program, aiming to onboard a significant number of new partners by the end of 2024.
- Program Enhancements: Recent updates to the CyberArk Identity Security platform offer MSPs simplified deployment and management tools, crucial for service delivery.
- Growth Potential: The global managed security services market is projected to reach over $60 billion by 2024, with identity and access management being a key growth driver.
- Channel Investment: CyberArk is increasing its investment in MSP enablement, including co-marketing funds and specialized technical training, to foster deeper channel relationships.
CyberArk's AI-driven analytics are a high-growth area, but still developing, unlike its mature PAM solutions. This positions AI analytics as a potential 'Question Mark' in the BCG matrix, requiring strategic investment to move towards 'Star' status.
The investment in AI analytics aims to enhance security insights, a market with increasing demand. Organizations are prioritizing AI security, with projected budget increases in 2024, indicating a fertile ground for CyberArk's developing capabilities.
CyberArk's AI analytics are in a growth phase, needing further development and market adoption to compete with established offerings. This strategic direction requires focused investment to capitalize on the growing demand for advanced security insights.
The success of CyberArk's AI analytics hinges on its ability to translate technological advancements into tangible market share gains. Continued investment in marketing and sales will be crucial for this segment to mature and achieve its full potential.
| BCG Matrix Category | CyberArk Offering | Market Growth | Market Share | Strategic Recommendation |
|---|---|---|---|---|
| Question Mark | AI-driven Security Analytics | High | Low to Medium | Increase investment in R&D, marketing, and sales to capture market share and move towards 'Star' status. |
| Star | Privileged Access Management (PAM) | Medium to High | High | Maintain leadership through continued innovation and customer support. |
| Cash Cow | Existing Identity Security Solutions | Medium | High | Leverage established market position for consistent revenue generation. |
| Dog | (Not explicitly identified in provided text) | Low | Low | Consider divestment or minimal investment if applicable. |
BCG Matrix Data Sources
Our BCG Matrix is built on verified market intelligence, combining financial data, industry research, official reports, and expert commentary to ensure reliable, high-impact insights.
